Every company faces the challenge of managing data, but have you considered the cost of losing it? Embrace the 3-2-1 Backup Rule – a foundation for robust data protection.
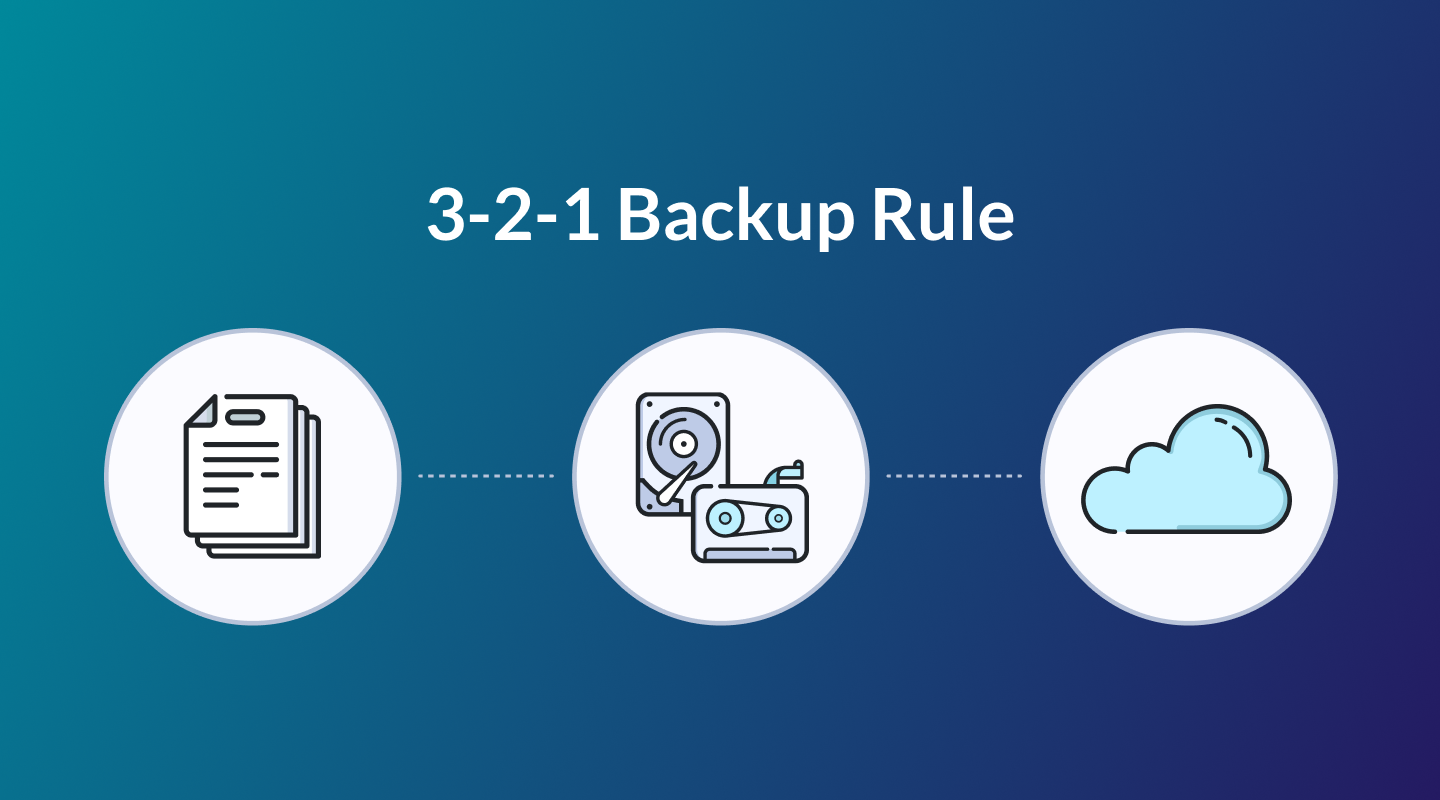
Every company faces the challenge of managing data, but have you considered the cost of losing it? Embrace the 3-2-1 Backup Rule – a foundation for robust data protection.

Azure Backup Center was revealed during Microsoft Ignite 2020. It will be later released as a single-pane-of-glass management and monitoring tool for Azure Backup vaults. The solution will allow you to monitor and configure your backups, restore data, and set a certain level of compliance, all from a single GUI. Read the short guide by Romain Serre, a Microsoft MVP, about Azure Backup Center, its benefits, and how you can preview it today.

IT administrators are always confronted with the problem of building innovative, fast, modern, and reliable IT infrastructure that fits the budget and saves resources for future growth. To commence, you should plan, select, re-plan, clarify goals, and so on ad infinitum in a vicious circle. However, the issue of guaranteeing the data safety will always be relevant on the agenda. Choosing a SAN (Storage Area Network) with the iSCSI protocol as one of the possible storage solutions will ensure data security and constant availability. In addition, this approach is cost-effective in terms of maintenance and support.

Nowadays, every company is doing its best to protect its data, which is pretty much its most valuable asset. As you know, data is vulnerable to unauthorized access and that’s when Microsoft BitLocker saves the day. BitLocker is the encryption technology from Microsoft, which makes possible to encrypt the Logical Volume on the transparent blade-based level (not physical disk). In this article, we will see how to encrypt Cluster Shared Volume (CSV) using Microsoft BitLocker to protect your data against unauthorized access.

In previous installments of this blog, we have deconstructed the idea of cognitive data management (CDM) to identify its “moving parts” and to define what each part contributes to a holistic process for managing files and more structured content. First and foremost, CDM requires a Policy Management Framework that identifies classes of data and specifies their hosting, protection, preservation and privacy requirements of each data class over its useful life. This component reflects the nature of data, whose access requirements and protection priorities tend to change over time.

In the previous blog, we established that there is a growing need to focus on Capacity Utilization Efficiency in order to “bend the cost curve” in storage. Just balancing data placement across repositories (Capacity Allocation Efficiency) is insufficient to cope with the impact of data growth and generally poor management. Only by placing data on infrastructure in a deliberative manner that optimizes data access and storage services and costs, can IT pros possibly cope with the coming data deluge anticipated by industry analysts.

In the previous post, we have explained and described business requirements and constraints in order to support design and implementation decisions suited for mission-critical applications, considering also how risk can affect design decisions.

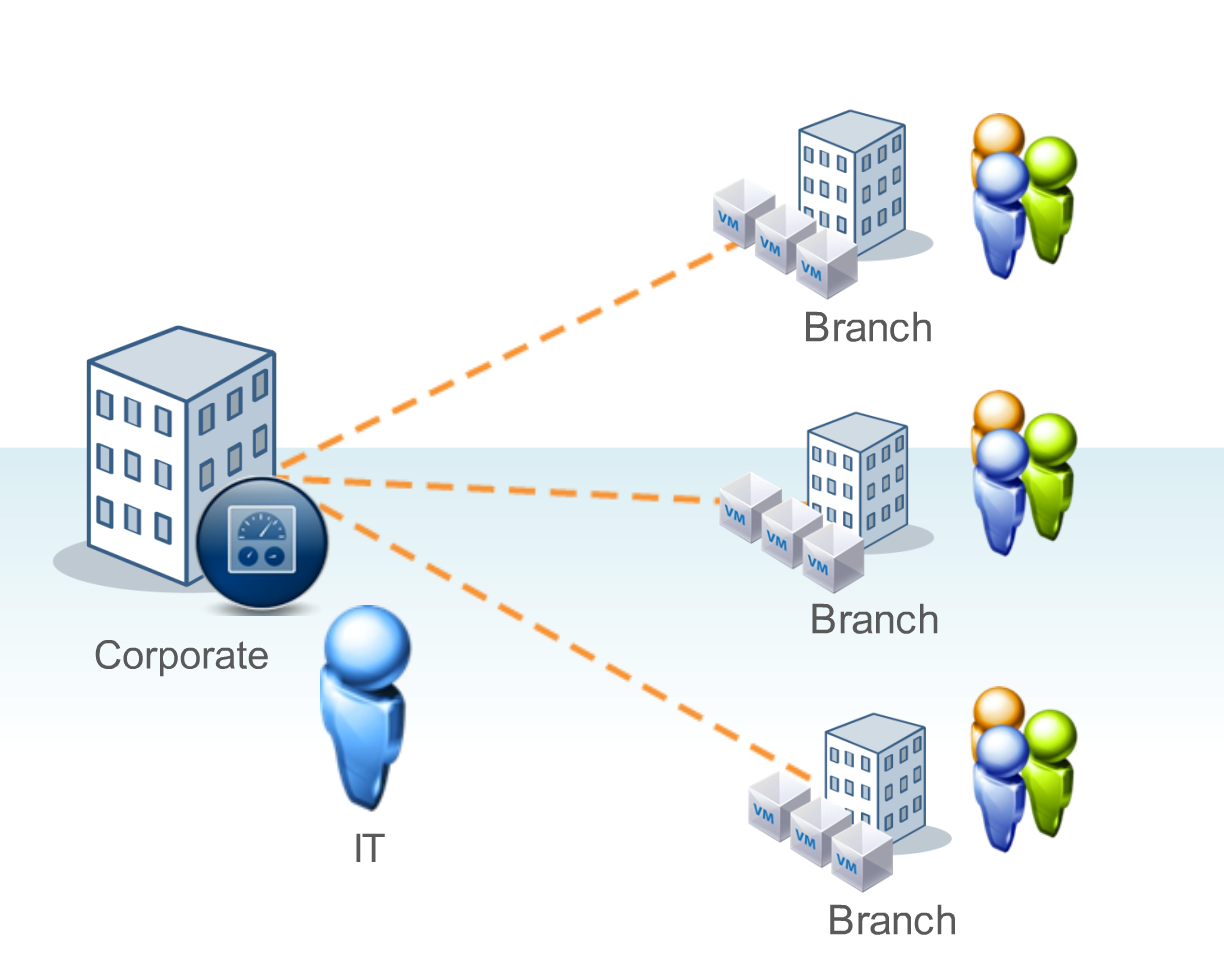
A Remote Office / Branch Office (ROBO) is an office located in a different site or a remote geographical area from another office (usually the headquarter or the main office). Several organizations have one (or more) main office, as well as remote offices in another city, country or continent. Many organizations today have in each remote office some local IT infrastructure, usually for data locality, but also for service local services.
After 2016 everyone can come to a certain conclusion that ransomware is a persistent phenomenon to reckon with from now on, with more sophisticated and innovative techniques to come. That is why it is crucial for every user and administrator to learn how to improve and protect their computer from ransomware.

With the release of Windows Server 2016, there’s a lot of new features that have been added to increase availability and security. One hot feature that will add a lot of benefits for small, medium and enterprise business environments is Storage Replica (SR). Be sure that’s going to help you in your Disaster Recovery Plan and protect your data against catastrophic losses.
